Introduction
In the previous article, we’ve played with the storage api and exposed few limitations, this time we will play with Key vault. In this article, we will see how we can interact with a Key vault through an ARC agent. With this article, we will:
- Expose some limitations
- Fetch a secret with REST calls directly
- Fetch a secret from Az-Keyvault module with an unusual way
- Play with the official secret management module
Limitations
For this article, I’ve created a demo Key vault (testacrfun) in RBAC mode, a secret (mysecrettohide) and I’ve granted the role “Key Vault Secrets User” to the ARC agent.
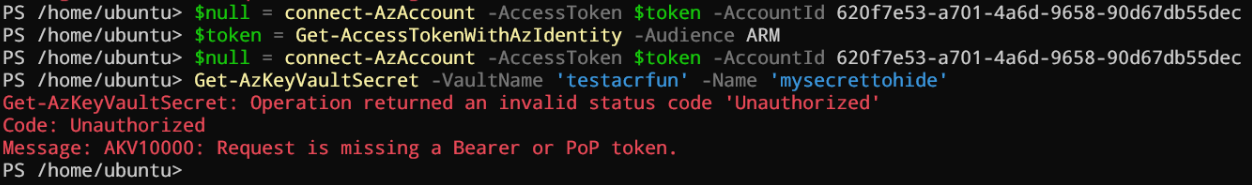
Like the previous article, we will connect with the accesstoken parameter and try to fetch the value of our secret.
$token = Get-AccessTokenWithAzIdentity -Audience ARM
$null = connect-AzAccount -AccessToken $token -AccountId <your arc appid>
Get-AzKeyVaultSecret -VaultName <your vault> -Name <your secret>
Here the result:
For the same reason as with the Az.Storage module (previous article), when you use connect-azaccount, you’re connected to the Azure control plane. When you request a secret, you use the data plane …
Use the REST api directly
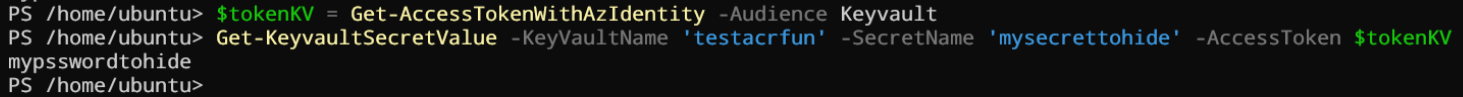
The first option is to use REST calls directly. You can for example load this function in memory and see the result.
$tokenKV = Get-AccessTokenWithAzIdentity -Audience Keyvault
Get-KeyvaultSecretValue -KeyVaultName '<your key vault>' -SecretName '<your secret>' -AccessToken $tokenKV
Here the result:
I’m using this technique very often, and it’s working really well. You can also fetch certificate and Keys the same way.
Use the Az.Keyvault module
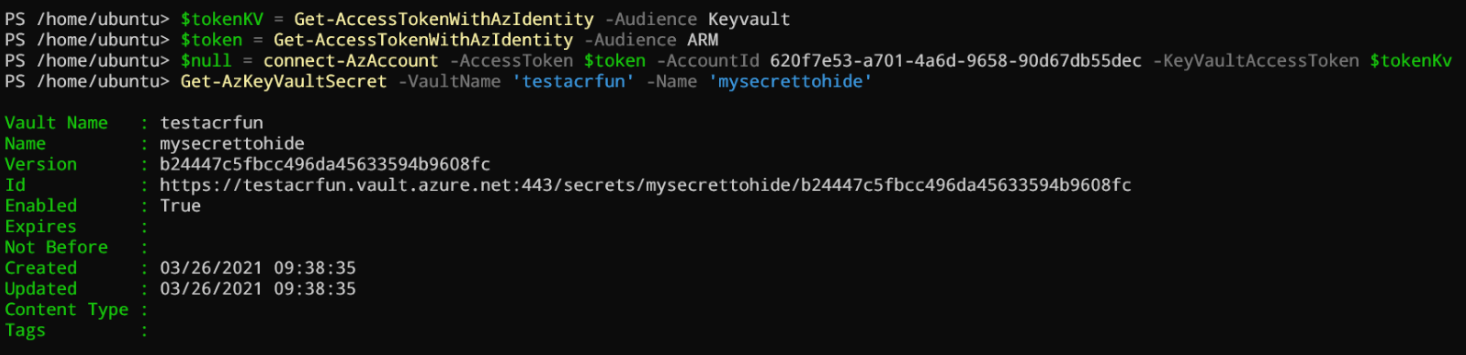
When I’ve read the code behind connect-azaccount, I’ve discovered by chance the parameter KeyVaultAccessToken (line 146). Let’s try!
$tokenKV = Get-AccessTokenWithAzIdentity -Audience Keyvault
$token = Get-AccessTokenWithAzIdentity -Audience ARM
$null = connect-AzAccount -AccessToken $token -AccountId <your ARC appId> -KeyVaultAccessToken $tokenKv
Get-AzKeyVaultSecret -VaultName '<your key vaul>' -Name '<your secret>'
Here the result:
This is really cool! The limitation we have with the Az.Storage module does not exist with the Az.keyvault module! We can connect with both control and Keyvault data plane token at the same time!
Secret management module
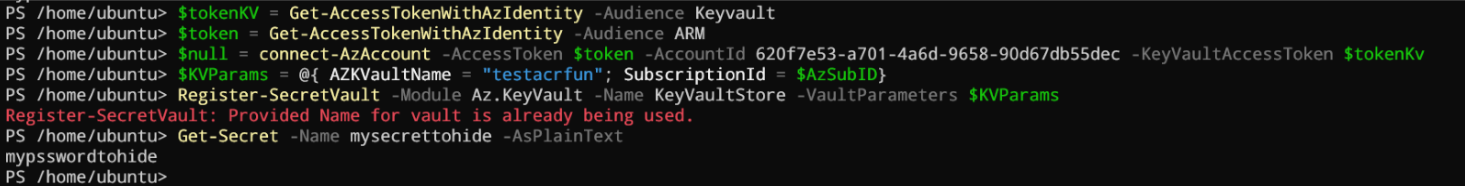
Let’s think a little. If we can connect to both control and data plane it means, we should be able to use the Microsoft.PowerShell.SecretManagement module no? Let’s try!
$tokenKV = Get-AccessTokenWithAzIdentity -Audience Keyvault
$token = Get-AccessTokenWithAzIdentity -Audience ARM
$null = connect-AzAccount -AccessToken $token -AccountId <your ARC appId> -KeyVaultAccessToken $tokenKv
$KVParams = @{ AZKVaultName = "<your vault name>"; SubscriptionId = $AzSubID}
Register-SecretVault -Module Az.KeyVault -Name KeyVaultStore -VaultParameters $KVParams
Get-Secret -Name <your secret name> -AsPlainText
Here the result:
I find this one so cool!
Conclusion
As you’ve seen during this article, ARC helps you to remove the chicken egg/secret 0 from your pipeline. I really hope Microsoft will add the same feature I’ve discovered with Keyvault to the storage module (and more in fact). See you for the next one.