Introduction
I’ve received recently a question which was “what would you do if you had to generate tokens (access and/or id) for non-coders?” In this case, the end user won’t be able to use MSAL or any other Oauth2 libraries, the idea is to click on a link, copy the token and paste it somewhere else.
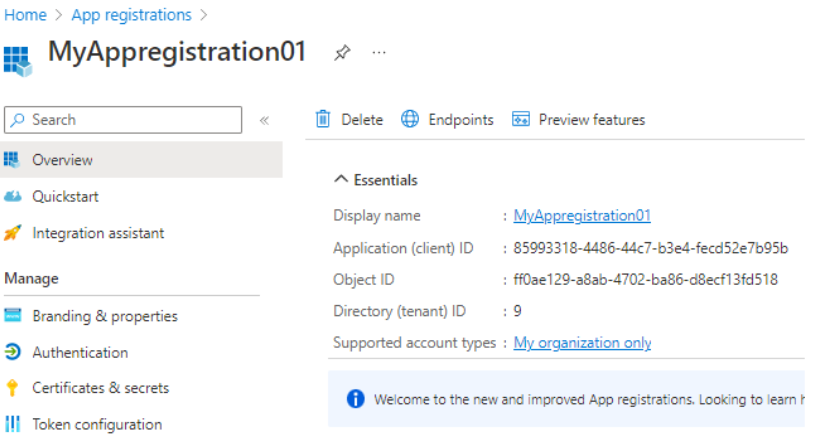
Create the app registration
Create a new app registration:
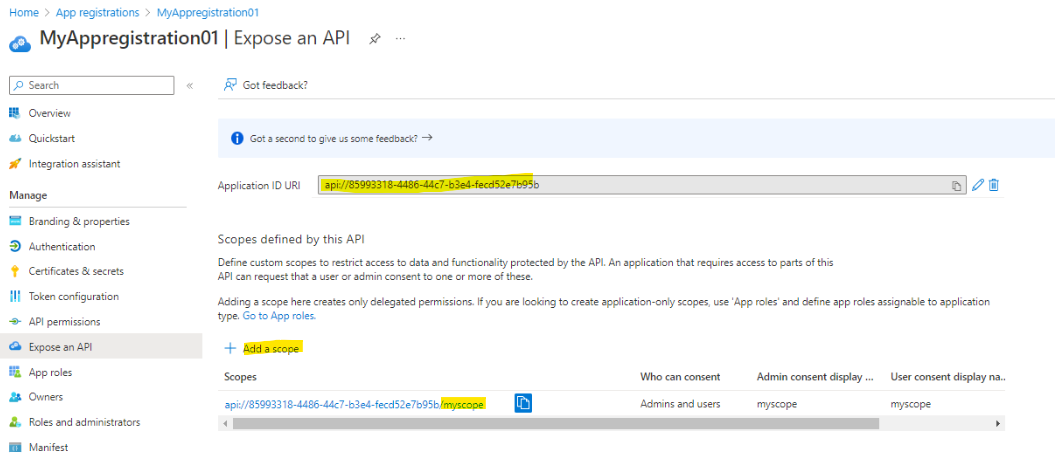
Click on expose an api (left menu). Click on set to tell AAD you want to expose something and add a scope in this case myscope:
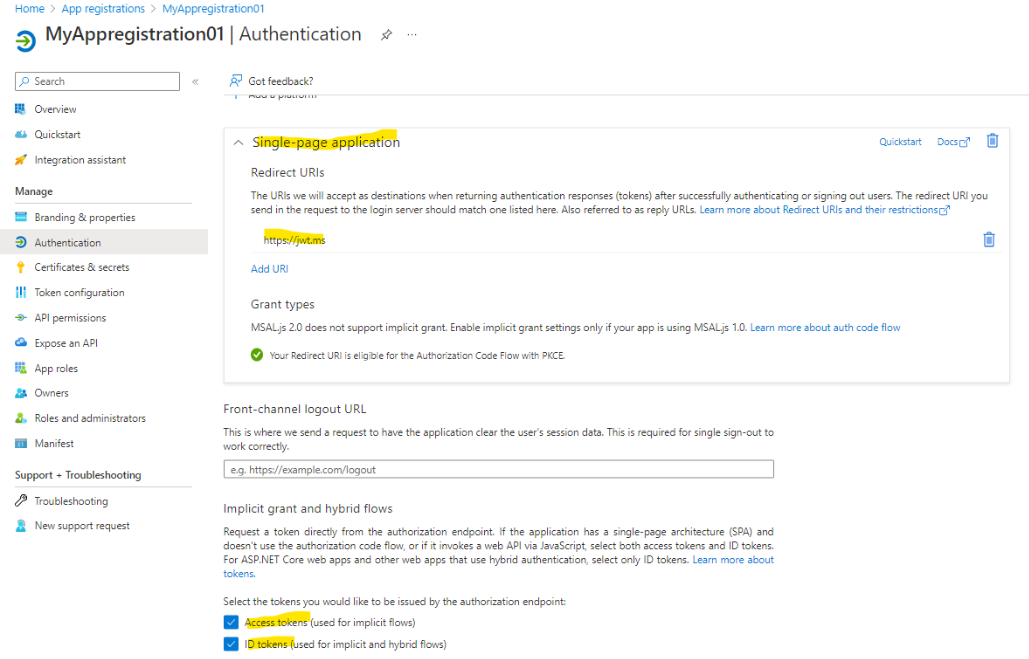
In the Authentication pane, select your platform, add https://jwt.ms as redirect uri and check Access and/or id token to enable the implicit flow.
That’s it, now you can secure your app with the enterprise application part where you can enforce who can generate tokens with the assignment required at yes.
Generate tokens
Now to generate tokens you have to create an encoded url you provide the link to your end user.
For Access token, create something like this:
https://login.microsoftonline.com/
In my case, it was:
https://login.microsoftonline.com/
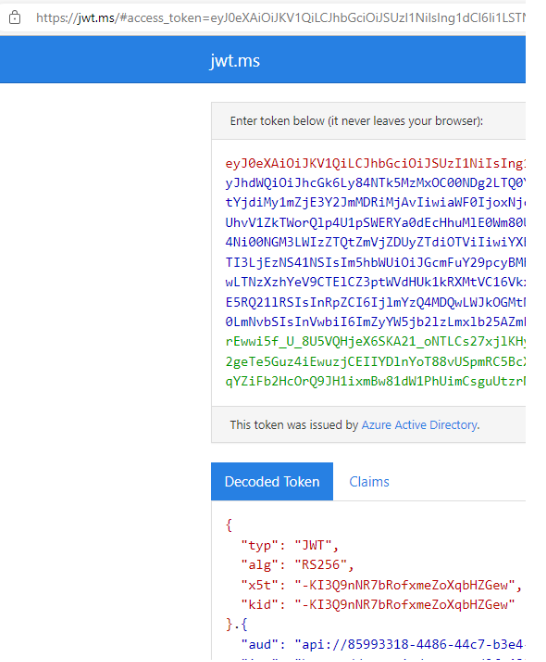
Once your users click on the link, the Azure Authorize endpoint will ask you your identity and then redirect the user directly to the jwt.ms page with your token:
If you want id token instead, you can provide a link like this one:
https://login.microsoftonline.com/
For example, in my case:
https://login.microsoftonline.com/
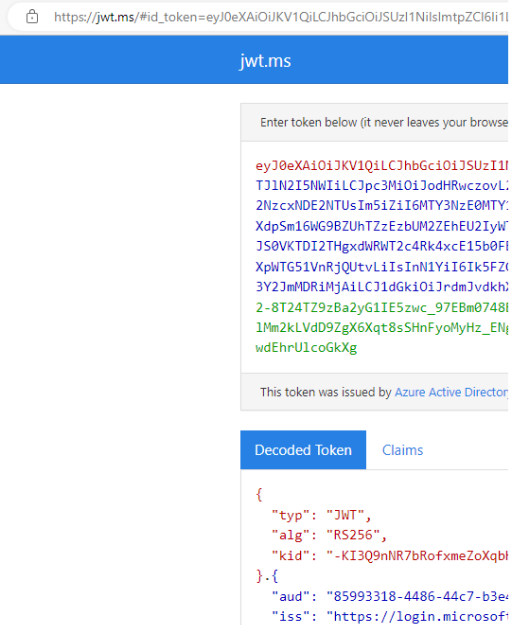
And again, jwt.ms will show you your id token:
Conclusion
Here is a quick and dirty way to generate tokens. Don’t forget you shouldn’t use this for prod environment.